Arctic EWS
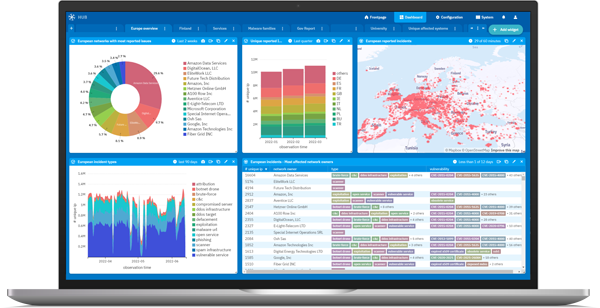
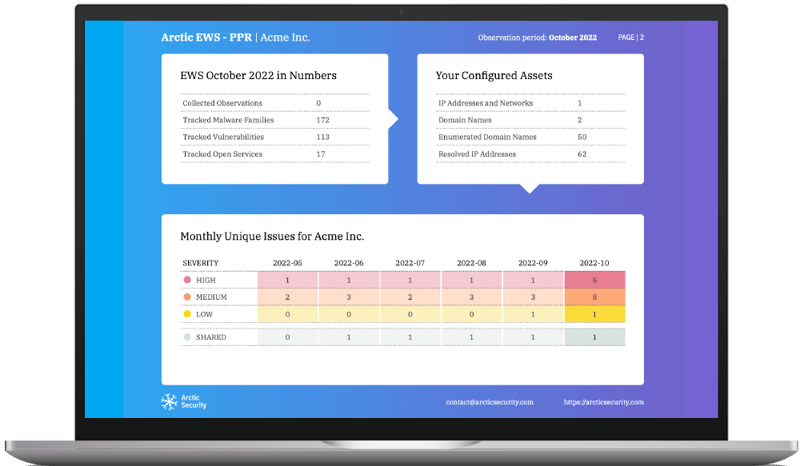
Your early warning service for cybersecurity issues. Arctic EWS generates security reports that give you the full picture of your network and the cyber threats it faces. It identifies the early signs of security breaches and vulnerable services so that you can prevent issues before they happen, and save costs in the process.
Get Early Warning