Stop cyber threats before they cause harm
Today's companies are using more and more digital assets. But while this creates new business opportunities, it also creates more cyber risks.
Organizations need to perform asset discovery on their networks before malicious actors find out what they can exploit. The most effective way to find cyber issues fast is with an early warning service.
This is where Arctic Security comes in. Of the malicious infections that will affect your network assets, traditional antivirus tools will catch fewer than half. Our suite of tools discovers cyber threats that traditional antivirus software cannot.
Reveal your attack surface
Do you have an email address? If so, then you have an attack surface - just like everybody else. But, unlike everybody else, you can get a comprehensive and detailed picture of your attack surface and reveal your vulnerable assets using Arctic Security’s suite of cyber tools.
Get tools designed by national security experts
Arctic Security has helped national cybersecurity authorities around the globe implement their cybersecurity notification services to protect critical infrastructure. Early warning services are a cost-effective way for companies to improve their cybersecurity and protect themselves against cyber attacks.
Why external cybersecurity monitoring?
Many data breaches go unnoticed. Information about vulnerable or compromised computers rarely reaches users who can take appropriate actions, and this gives cybercriminals opportunities they might not otherwise have.
Our early warning service Arctic EWS generates security reports that clearly show you every threat in your network so you can fix them all and avoid potentially fatally expensive breaches.

Simplified cybersecurity
Reducing your cyber risk shouldn’t be complicated. The goal is to reach as few notifications as possible. It’s that simple. That’s why we built Arctic EWS; to provide you with easy-to-digest and actionable information that enables you to eliminate your issues.
You also shouldn’t have to hire expensive cybersecurity specialists to be safe. Instead of being overly complicated, Arctic EWS actually helps you to build your expertise regardless of your starting point.
A proven track record
Early warning services are not a new idea. They have been used successfully in cyber defense to protect critical national infrastructure and improve cybersecurity for companies. Until now, these have been implemented by National Cyber Security Centers (NCSCs) and Computer Emergency Response Teams (CERTs) in many countries.
We developed the technology platform used in these established national warning systems and packaged it to work just for you.
Unrivaled quality
Security reports are only as good as the information they use, and we use the best you can get. Every day, we see 15 million cyber threats affect 80,000 organizations around the world. Arctic EWS provides better coverage for multinational companies than even some national services.
Protect your organization now
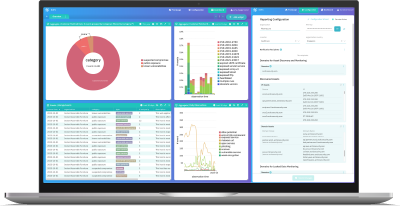
Arctic EWS
Cybersecurity issues are often unknown to businesses but visible to the world, which leaves the door open for potential cybercriminals and hackers. Arctic EWS identifies the early signs of security breaches and vulnerable services so that you can prevent issues before they happen.
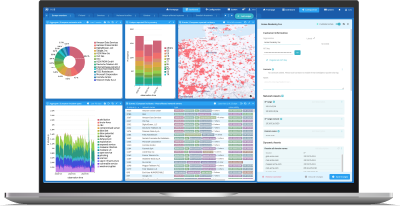
Arctic Hub
To make sound cybersecurity decisions, you need actionable threat intelligence. Arctic Hub is a powerful cybersecurity automation tool that collects, harmonizes and packages threat information quickly and effectively.
Recommended by
TAG Infosphere
TAG Infosphere, the world's leading next-generation cybersecurity analysis firm, has announced the addition of Arctic Security to its TAG Exchange platform. The TAG Exchange highlights the cybersecurity industry's most creative and innovative solution providers, driven by AI and SaaS technology; it showcases the industry's top performers, offering valuable resources to enterprises and government agencies seeking to enhance their cybersecurity posture.
Latest from the blog
Want to know more? Contact us
Looks like you are proactive about cybersecurity. We like that! Let us know what you want to accomplish, and our team team will be in touch. Together, we can work out the best way to help you.