100% automated cybersecurity
Offer your clients unbeatable protection
Today, cybercriminals sometimes find themselves one step ahead of companies. Our solution helps to close that gap by taking the opportunities to commit cyber attacks away from them.
Arctic Hub is an early warning solution that automates the finding and processing of threat observations. You can use the Hub to provide your stakeholders with tailored, up-to-date threat information. The highly automated process is easy on your resources and easy to implement. All that’s left for your customers to do is to act on your information.
Arctic Hub is a powerhouse…
We built Arctic Hub to work even under the most challenging conditions. It automates your cybersecurity using seriously huge amounts of data, so you can be confident that you’re not missing anything. Arctic Hub scales to national-level needs, allowing you to serve tens of thousands of customers.
Arctic Hub allows you to share only the relevant information matched to your clients. Our incident notifications are directly actionable and let recipients know which security issues to fix. This stops you and your customers from being overwhelmed with threat information and allows you to focus on what matters.
…that gets better over time
Arctic Hub observes trends and malicious campaigns and tracks progress to improve defensive cybersecurity. This allows our clients to understand the vulnerabilities and weak points in their infrastructure already visible to cybercriminals.
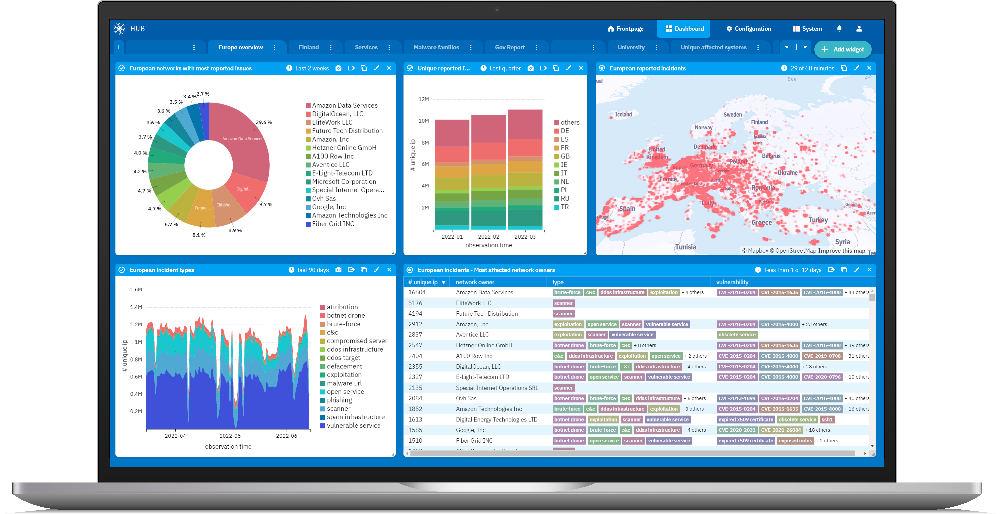
The Arctic Hub dashboard displays real-time information on the threats your customers have faced. It allows you to map the collected information and classify it by industry sectors. With better visibility over your infrastructure, you improve the cyber defense of your stakeholders.
Helps your stakeholders take action.
Organizations that deal with hundreds of notifications a day need a way to prioritize and automate their management. Arctic Node collects cyber threat intelligence from Arctic Hub and other sources to help you maximize your defensive cybersecurity posture.
Key features
Automated intelligence sharing
Customers value the threat intelligence data that’s relevant to them. Arctic Hub automatically maps threat data to your customers based on their internet presence so you can specify in detail which types of threat intelligence packages you want to send to whom. You can share packages via email reports or direct API access.
Harmonized data
When it comes to information, the better the sources you have, the more confident you can be. Arctic Hub automatically harmonizes incoming data so you can be selective about the sources you use for your threat intelligence. This harmonized data is formatted so that it can be easily sent for further analysis, processing and mapping to customers.
True situational awareness
Better situational awareness helps you set up cybersecurity KPIs to monitor improvements. The Arctic Hub dashboard shows real-time information on threats your customers have faced. You can split threat data using factors such as customer type, geographical area, malware type or observation time.
Automated attack surface discovery
To make your service as effective as possible, you need to know what works for your customers. Arctic Hub shows you detailed feedback on which customers access which threat intelligence packages at which times. This way, you can give them more of what they need, and less of what they don’t.
Feedback-based optimization
To make your service as effective as possible, you need to know what works for your customers. Arctic Hub shows you detailed feedback on which customers access which threat intelligence packages at which times. This way, you can give them more of what they need, and less of what they don’t.
Integrate a range of feeds
Out-of-the-box, Arctic Hub can collect raw threat data from around 100 commercial and open-source threat feeds.
Here are just a few examples of feeds you can integrate, with many more supported.
Arctic Hub includes flexible APIs so that it can also process data that you produce in-house and automate getting it to your stakeholders.

Use cases
for Arctic Hub
Situational awareness and KPIs
Arctic Hub shows you real-time information on the threats and data breaches your customers have faced. You can also see how the threat data has been divided into different factors such as type of customers, geographical area, type of malware or observation time.
Automatically alert your constituents
Cybersecurity authorities, CSIRT teams and ISACs can tap into a wealth of actionable and reliable abuse information. This information can alert your stakeholders on compromised or vulnerable systems and help them to remediate them in an efficient manner.